Highlights:
- GreedyBear crypto scam used 150 weaponized Firefox extensions to steal wallet credentials.
- The group deployed nearly 500 crypto-targeting malware programs.
- All attacks operated through a single coordinated command server.
A cybercrime organization called GreedyBear has executed a significant crypto theft. Koi Security, a cybersecurity firm, has associated the campaign with more than $1 million in stolen funds. The group used a fake wallet extension, crypto-focused malware, and scam websites. According to the researchers, the attack demonstrated a coordination of a scale never seen before in the crypto theft market.
The attack featured over 650 malicious programs against crypto wallet users. It included 150 weaponized Firefox extensions, which resembled popular wallets such as MetaMask and TronLink. These fake extensions initially looked harmless in order to be permitted in the Firefox scrutiny. Once they were trusted, they were patched with code to steal wallet passwords and private keys.
💥BREAKING NEWS 💥
GreedyBear just took crypto crime to a new level—over $1M pilfered using 150+ fake Firefox wallet extensions, malware, and scam sites. It’s like they built a fraud factory.
Have you double-checked your extensions lately? 👀 #Crypto #Web3 #Security pic.twitter.com/fZS8o4fPDo
— Cheeky Crypto (@CheekyCrypto) August 8, 2025
Multi-Vector Strategy With Extension Hollowing
Koi Security detailed a tactic called “Extension Hollowing” in the GreedyBear crypto scam. To establish trust, the group opened new accounts at the marketplaces and imported harmless tools. In addition, they flooded listings with fake positive reviews to make themselves credible. They later interchanged the code with their malicious payloads, maintaining the same naming and ratings.
This method allowed the criminals to bypass the security checks when making initial submissions. After the extensions were weaponized, they forwarded IP addresses and wallet credentials to a control server. The same infrastructure was used to coordinate ransomware demands and to host phishing websites. As security specialists affirmed, the server also processed data related to malware operations.
The malware component of the campaign contained nearly 500 Windows executables. Such files used to be shared largely through Russian websites that provided pirated software. Families of malware, such as LummaStealer and Luca Stealer, attacked wallets and encrypted devices. Hackers demanded payments in cryptocurrency to recover data access.
Scam Websites and AI-Driven Scaling
The third method of attack was based on sophisticated imitation websites. Such websites copied digital-wallet brands, hardware devices, and wallet repair services. They were finely tuned landing pages that were aimed at harvesting sensitive user information. In reality, they served as data harvesting tools for the threat agents.
All the aspects of the attack were found to be linked to a single IP address. With this single hub, GreedyBear was able to coordinate and expand operations effectively. The presence of indicators of AI-generated code hinted at the ability to expand new attacks rapidly. Consequently, this automation made detection and blocking much more challenging for defenders.
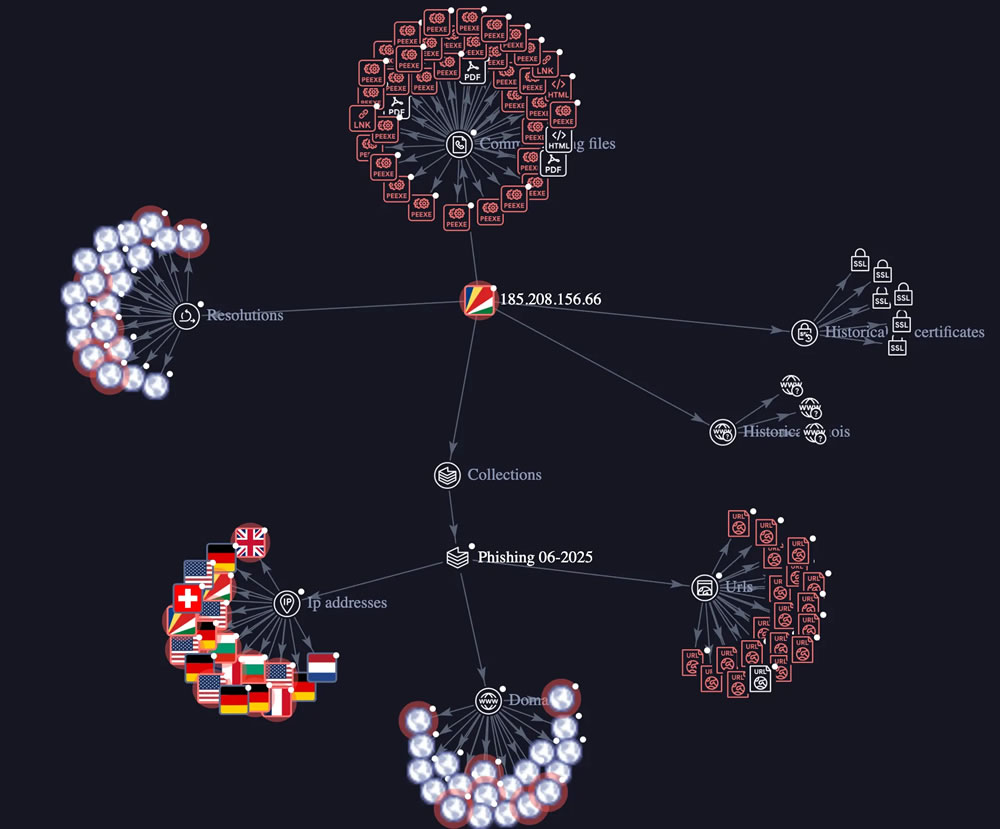
The GreedyBear crypto scam evolved from the smaller Foxy Wallet campaign. The campaign initially involved only 40 malicious Firefox add-ons. The scale has tripled, pointing in the direction of expansion to Chrome. Security researchers indicate that Edge and other browsers may be targeted soon.
Crime associated with crypto is on the increase in the sector. In July alone, 17 different cases of hackers stealing $142 million occurred. Blockchain security company PeckShield noted that the losses in July increased by 27% compared to June. Although the numbers amount to less than the July 2024 figure of 266 million, they are still substantial.
Best Crypto Exchange
- Over 90 top cryptos to trade
- Regulated by top-tier entities
- User-friendly trading app
- 30+ million users
eToro is a multi-asset investment platform. The value of your investments may go up or down. Your capital is at risk. Don’t invest unless you’re prepared to lose all the money you invest. This is a high-risk investment, and you should not expect to be protected if something goes wrong.






